
There are numerous hacking techniques that have surfaced on the internet. Whether through ad links, pop-ups, or hiring a hacker, there are many bad artists out there who will do anything to trick a user into disclosing personal information or to profit from our human errors. However, it is critical to be aware of a tactic being used by hackers and scammers to obtain the information they seek. This technique is impersonation.
To elaborate, hackers are now scamming people by impersonating business owners, managers, team members, recruiters, and other employees via phishing emails, tricking end-users into believing the emails are from those within the workplace. This, however, is ideal for hackers to be trusted as a credible sender and gain access to your company's private information through human error.
Let me explain some of the techniques hackers use to gain your information.
-
Impersonation as a manager or business owner.
Recently, a phishing email, with a technique called ‘double-barrel phishing’, was sent to an Infiniwiz employee. The email seemed to be from our manager, Alek Pirkhalo, where the hacker asked the employee for their cell phone number to send information to the employee. The hackers will essentially send the first email in an urgent tone for you to send out whatever information they need to hack you.
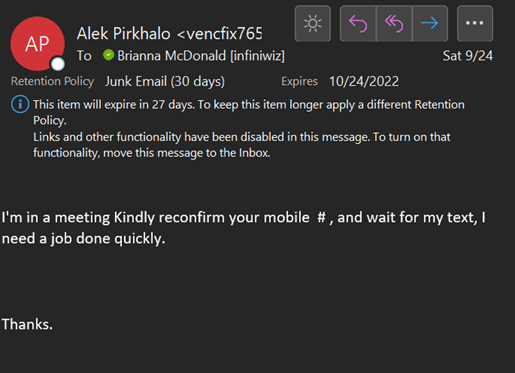
Later, the hacker will send a follow-up email. The second email will be sent out a few days later to try and gain the same information if one doesn’t reply.
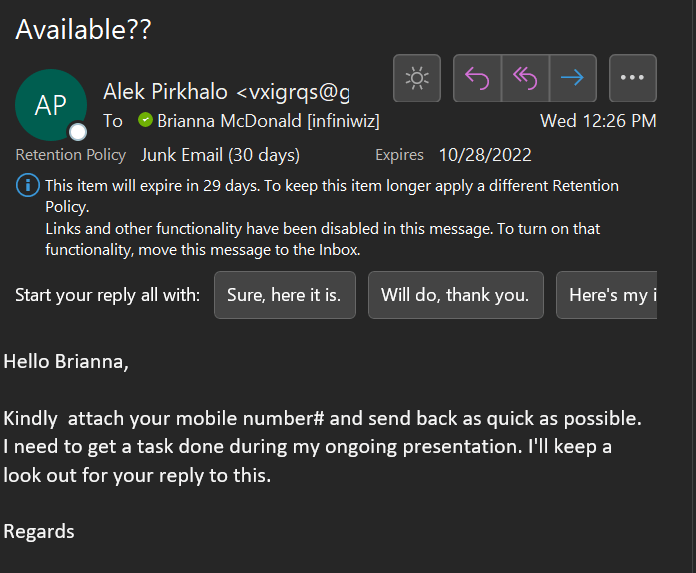
Many employees see an email from their manager and immediately want to complete the task at hand, not realizing who the email is from. The employee saw that the email in the From field wasn't Alek's email. This is how she knew it was fake right away.
In addition, as seen in the email, hackers will use an urgent tone or send a follow-up email to make employees feel pressured to complete that specific task. This rush can lead to human error, such as approving or allowing malware/hackers access to business information or even your own personal information as an employee.
-
Dual Phishing
Dual phishing is a new technique that hackers have begun to employ. It is a conversation between two hackers who are posing as business team members, as the name suggests. If you are an employee, you may suddenly receive emails in which you are cc’d in a conversation thread. For example, you could be viewing a conversation thread that you think is between your manager and another team member. They have a conversation in which they respond and start a conversation. As an example, consider the following:
Manager (hacker): Hello John. We have received an email stating that we have a bill due from last month. Do you see previous payments with this company?
John (hacker pretending to be your co-worker ): Hello. Yes, we have previous payments with this company. We need to pay this bill as soon as possible.
At some point, they then involve an employee from the company to do a certain task.
Manager: Thank you for checking, Jane, can you make sure this bill is paid as soon as possible? The invoice was due last month, so it’s urgent! Wire the payment to their US Bank account 235445664...
Because it is two of their team members conversing, the employee may believe that the conversation is legitimate. In reality, these were the perpetrators. Because they had previously seen the conversation with the sender using the name of a team member she knew, the conversation appears more legitimate, allowing hackers to gain access to your company data or steal your company money.
-
Impersonation as an HR or a business recruiter
There were cases where scammers have been impersonating job recruiters, where people who are desperately looking for a job would be hard to ignore. These hackers are using appealing titles such as “higher, paying jobs” to bring specific audiences in. Last year, one of our clients who worked as an HR was impersonated and the scammer created a fake recruiter profile on a job search website and invited people who were looking for jobs in a medical-specific field. Additionally, the con artist used her name and sent out emails for people to apply to the company where she worked at. Additionally, the bad actor asked those applying to pay a fee to access the application form. For a while, the HR rep had no clue these emails were being sent out under her name. Overall, while this tactic can trick users searching for their job, this also hinders the credibility of companies and spreads false information on their hiring program.
Watch out for the following hacking tactics in emails.
• Urgent tones that rush you to finish a task
• Lack of an email signature
• A sender address you don’t recognize
• Errors in email addresses
• Certain requests and procedures that seem unusual
• Typos within the email
Moreover, be on the lookout for phishing attacks that are trying to attack your company. These phishing emails are getting more legitimate as hackers take more time to make emails look more real. The more success they have with tricking users, the more money they will gain.
Take some time to read more about phishing attacks in our recent blog here.
The Infiniwiz technical team in the Chicagoland area takes a proactive approach to your cybersecurity. We set up the right IT protocols and help you put in place the employee procedures that will keep your data and network safe from online predators.




