In today's technological environment, threats against your data are rising as malicious attackers find new tactics to infiltrate your systems.
Here are a few facts:
- 43% of all cyber attacks are targeted at small businesses.
- About 60% of these firms close their doors within six months of a cyber attack.
- In recent studies, it generally takes a company six months to realize they've been hacked.
(thrivedx).
While these facts may seem scary, users can implement security measures to safeguard their data and systems where there is the least likely chance of being attacked.
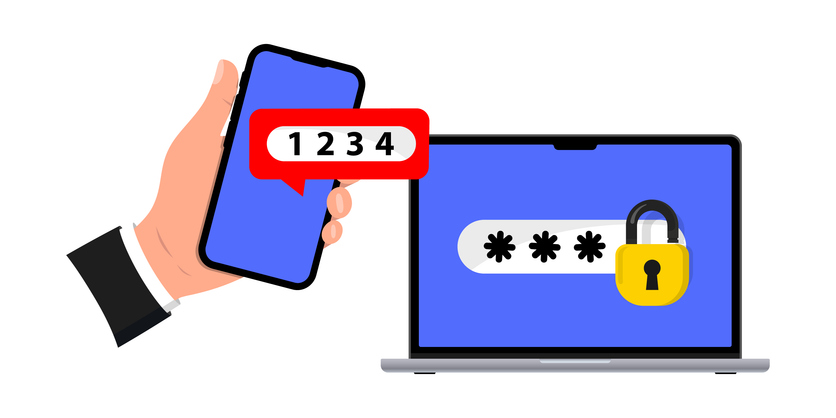
One security measure that is now widely used and often mandatory is multi-factor authentication (MFA).
So, what is MFA?
Multi-factor authentication is a method in which a user gains access to a website or application only by successfully inputting two or more pieces of evidence within the authentication process.
What are some ways you can approve?
SMS Verification:
A code is sent to a user's device via text message, and the user must enter the code to verify their identity.
Email Verification:
An email with a verification code or link will be sent to a user's email address. The user then must click the link or enter the code to confirm their identity.
Authentication Apps:
Users can install authentication apps, such as Google Authenticator or Microsoft Authenticator. These apps generate timed, one-time codes that users must enter to authenticate.
Push Notifications:
Users will receive a push notification on their device, prompting them to approve or deny the login attempt. However, ensure the push notification is legit from a program or website you are trying to use. Hackers now utilize push notifications to deceive users and hack into their systems.
Read more here: Unveiling MFA Fatigue: A New Threat Landscape.
Voice Recognition:
In some cases, users may be required to speak a passphrase or even answer security questions for verification.
If you are aware of MFA or have it yourself, many people get frustrated only because they feel it takes too much time to approve, not once but twice, to get into a website or program; in many cases, we have seen users wanting MFA turned off.
However, MFA is imperative for the security of your data.
Why is MFA necessary?
Enhanced Security:
MFA is necessary because it adds an extra layer of security when logging in. Traditional authentication methods such as passwords are increasingly vulnerable to cyber attacks such as phishing, brute force attacks, and credential stuffing. With MFA, this mitigates these risks by requiring users to provide multiple verification forms before granting access to an account or system.
Protection against password attacks:
MFA significantly reduces the risk of cyber-attacks because even if a hacker obtains a one-factor method such as a password, they would still need the additional factor (e.g., a code sent to a mobile device) to gain access.
Compliance Requirements:
Many industries require companies to have MFA to ensure the security of sensitive data. Compliance standards such as PCI DSS (Payment Card Industry Data Security Standard) and HIPAA (Health Insurance Portability and Accountability Act) require organizations to implement MFA as part of their security measures.
The same goes for the Safeguards Rule for financial institutions and insurance companies when businesses try to get cyber security insurance. Some insurance companies won't provide coverage without MFA in place.
Adaptation to Evolving Threats:
As cyber threats evolve, MFA provides an adaptable security measure to help organizations stay ahead of attackers. By requiring multiple forms of authentication, MFA can effectively mitigate emerging threats.
How can Infiniwiz assist you with implementing MFA?
As a Managed Service Provider, Infiniwiz strongly believes in protecting the company's sensitive data. Therefore, one of the services we provide is managing your MFA.
Let me explain.
This mandatory service is one of the best practices a user must have. We use this security measure to secure emails and other essential software programs when opening them. Therefore, we will ensure that MFA protects all your programs and websites. If you have any questions regarding the extra level of protection, we are here to help.
Additional Note:
Beware of human error.
Having Multi-Factor Authenticator doesn't automatically protect you. We had a user's mailbox broken into even though she had MFA implemented. How did this happen? After malicious actors guessed her credentials, they tried to log into her mailbox. This triggered the mailbox owner to receive an MFA application notification on her mobile phone stating, "Do you approve access? Yes or No." At the time, she was in the middle of her work, and when she kept getting the notification, she eventually clicked "Yes" to get rid of the annoying popup. Thus, she was a victim of "MFA Fatigue" used by attackers.
Human factors are always important to consider. You still need to be careful. Ensure your team members are involved in the ongoing security awareness and training program.
Overall, MFA is imperative for protecting your company's data. Ensure that you have MFA implemented for all your websites and programs, but also remember that malicious actors are waiting for one wrong move of human error. Be vigilant within your digital tasks and actions.
If you have any questions, feel free to contact us!