
Earlier this week, we discussed how QR codes have become increasingly popular in being convenient, contactless, and effective in receiving information and getting tasks done more effectively.
Malicious actors also know that QR codes are convenient and are now using them to assist with phishing attacks sent to users' emails. It is important to note that this new phishing technique is becoming more prevalent where users are seeing it in their inboxes. That's right, they are even bypassing email spam filters! Let me explain.
Recently, one of my associates received an email that seemed to have been from Microsoft Authenticator stating that they have rolled out new updates to mitigate email theft on the user's Microsoft Office 365. The email looks legitimate and even has a QR for the user to scan to make the process of setting up multi-factor authentication much easier without the time-consuming steps of manually doing it yourself.
Looks pretty legit, doesn't it?
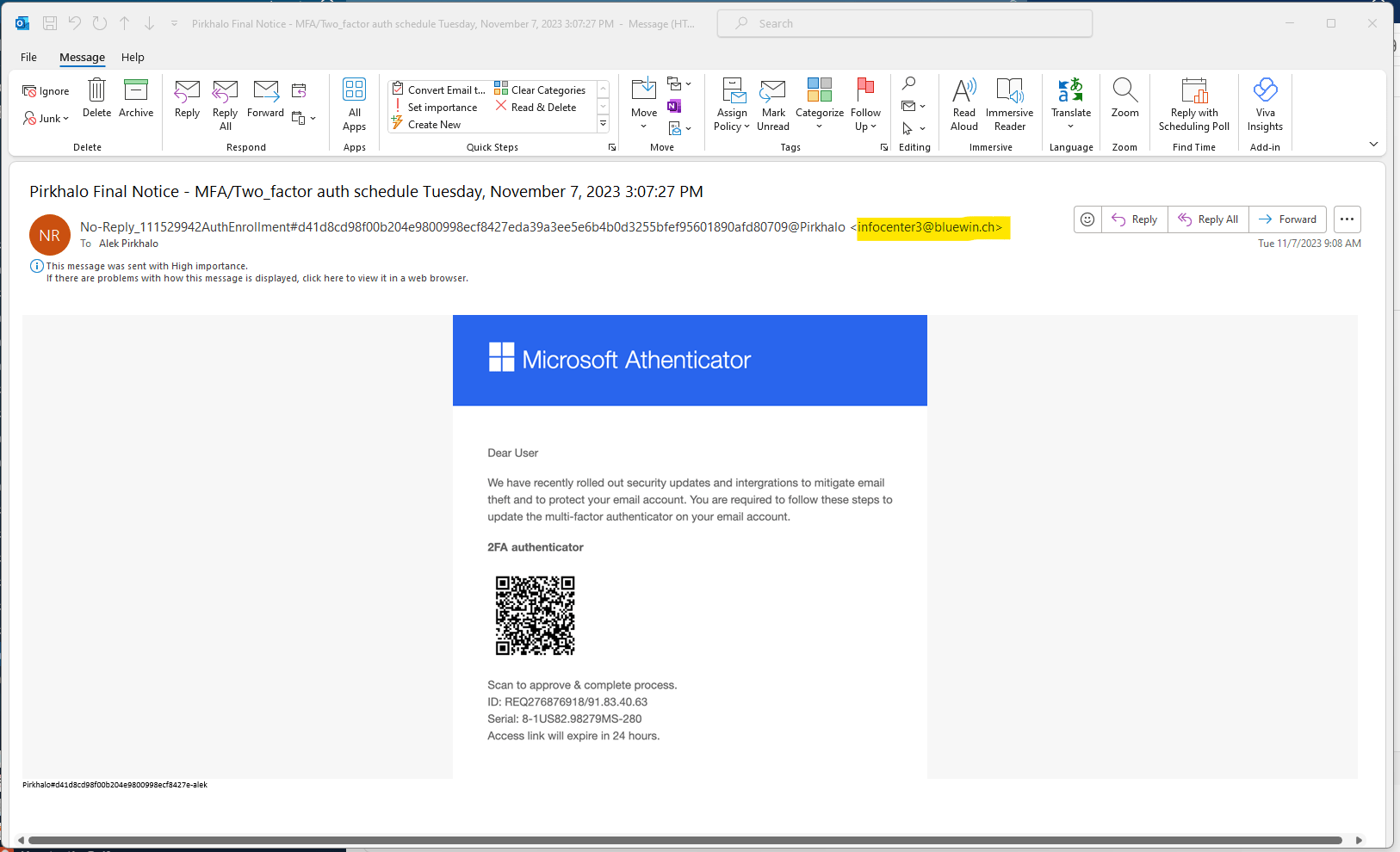
So, how did our engineer spot that this was a phishing attack?
Improper spelling and grammar usage
Within many phishing tactics, there are instances where the malicious actor may have spelled words wrong or used incorrect grammar usage. In this example, you can see that the word "authenticator" is spelled wrong in the title. When reading emails that may seem suspicious, ensure that you check for issues such as these.
The sense of urgency
At the bottom of the email, a message states, "Access link will expire in 24 hours." This is a common tactic malicious actors use to pressure the recipient into taking quick action. They hope that by doing so, individuals may not thoroughly evaluate the legitimacy and rush to click on links or provide sensitive information.
Obscuring sender identity with a long email address
In the example above, you can see that the sender's email address is very long. Malicious actors intentionally extended the sender's address, making it overly long. This is so that users can only see the part before the @ sign. This tactic is designed to obscure the non-Microsoft email address ending so that the recipient thinks it is a legitimate email from Microsoft.
So, how are these phishing emails bypassing spam filters?
It is essential to emphasize that this particular email contained virtually no text; instead, it consisted of a single image in the email body with no links and no accompanying textual content. Abnormal Security states, "7% of all attacks that bypass native spam/junk filters use QR codes." Therefore, it makes it easier to bypass spam filters since no actual text, such as links, can be scanned.
As QR continues to be used in different aspects, malicious actors will continue to use it as a source for their phishing techniques. While QR codes are now used as part of the process for multi-factor authentication, it may be hard for a user to determine when an email is not legitimate. When reading emails, watch out for bad grammar and suspicious email addresses/links when opening your emails.




